You can listen to or watch this article here:
The most important thing to know when learning about cryptocurrencies is their original purpose [1].
Cypherpunks
Since the late eighties, a growing group of Libertarian scientists, engineers, computer scientists, and philosophers, called Cypherpunks [2], were discussing and debating ways to use cryptography to increase their privacy in a world that was going to be increasingly dominated by computers and the internet.
Cypherpunks started a mailing list [3] in the early nineties and in it they proposed and argued for different systems that could be used for their purposes. The goal was always to create a sort of secure environment in cyberspace, that would be protected from government and corporate spying, using cryptography.
As the discussions and proposals evolved, in time three main themes developed: The original goal of privacy [4]; the need for a form of money [5] in this protected cyberspace; and smart contracts [6] to enable enforceable transactions between anonymous strangers without the need of trusted third parties.
At the base of the purpose of the cypherpunk effort was this last concept: Avoiding trusted third parties by means of trust minimization [7] [8].
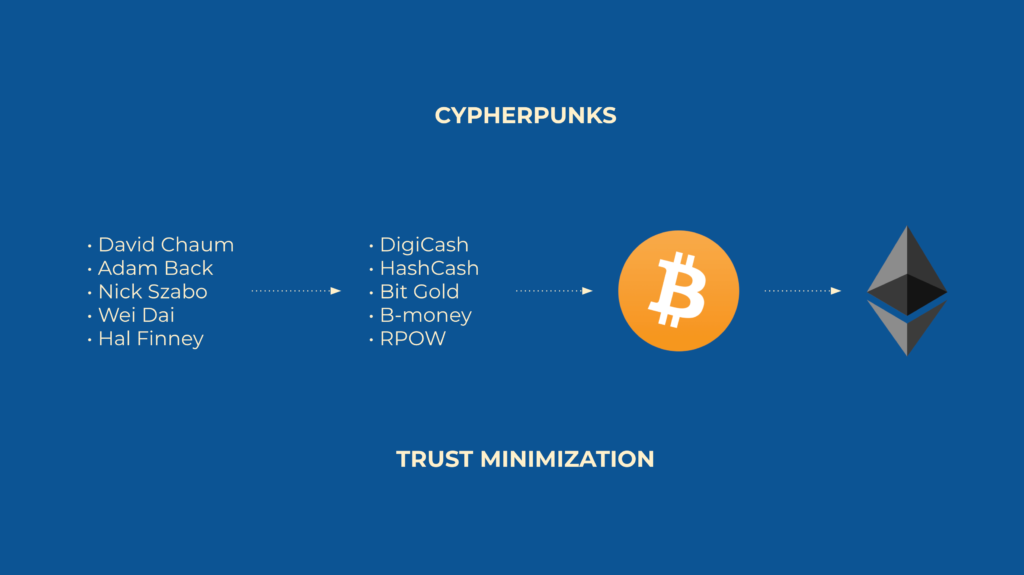
Precursors of Cryptocurrencies
In the specific search for a form of currency that was secure in a pure internet environment there were several efforts.
DigiCash
DigiCash [9] was the earliest attempt at digital money. Created in 1989, it was centered around privacy of transactions.
Its founder, David Chaum [10], was in fact one of the precursors of the cypherpunk movement through his philosophy and ideas about using cryptography in the public domain to protect the privacy of everyday online interactions.
DigiCash was promoted to banks at the time, but the effort ended in 1998 with the closure of the project.
Its main drawdowns were resistance by financial institutions; that it depended on pegs to regular forms of government cash to guarantee the digital units; and that, although the system guaranteed privacy through a technology called blind signatures [11], it still ran on a centrally controlled server, making it vulnerable to the trusted third party who managed it.
HashCash
HashCash [12] was created in 1997 by Adam Back [13], a cypherpunk, to prevent email spam. It is not really a currency or an attempt to create money in the online world.
However, its underlying technology of forcing computers to do a lot of work, in the form of computational cycles, called proof of work [14], to perform an action, is at the core of what would become the future cryptocurrencies we know today.
Bit Gold
Bit Gold [15] was invented and described by Nick Szabo [16], also a cypherpunk, between 1998 and 2005. This was the first model for a fully independent cryptocurrency. The system incorporated the ideas of a peer to peer network of nodes to manage a distributed ledger [17], and proof of work based on a proposed computational puzzle.
It provided detail as to the operation of the system, and specifically imitated how the production, scarcity, and value of gold worked in the real world. Hence, its name.
Bit Gold included the process of proof of work as the mechanism for participants to show that something of value, by way of cost, was created to be used as a pure digital currency. Then, it required the time stamping of the proof of work in a distributed fashion, and used the network of nodes to manage the ledger with accounts and Bit Gold balances, as a property titles system [18], for users to hold, track, and transfer their currency.
Another innovative idea of Bit Gold was to use the previous proof of work as the puzzle to solve the next creation of Bit Gold. This would eventually form a chain of solved puzzles, very much like what today is called a block chain, or blockchain, in the cryptocurrency industry.
This chain also served as an easier way for participants to assay whether the currency they bought, or they were being paid in, was not forged.
The other important feature of Bit Gold was not only to use the proofs of work as the base elements of value, but to use a Bit Gold market to form the price of such irregular proofs, so they could be grouped in generic bundles to make the digital commodity more standardized and fungible.
On top of these bundles, which imitated ingots of gold in the real world, a system of tokens was to be created to make the assets divisible and transferable, and thus more suited to be used in a digital economy.
The peer to peer network consensus mechanisms at the time protected against collusion attacks and double spends to a threshold of 33% of the nodes in the system. This is called the Byzantine fault tolerance in computer science [19].
The Byzantine fault tolerance problem means that if 33% of the node operators agree to corrupt the network, by reorganizing the history of transactions for example, they could do it as the others had no way of stopping or controlling such actions in a distributed, totally decentralized system.
Even if it was a very advanced proposal for its time, Bit Gold also had some drawdowns. These included the problem that the Bit Gold market was very difficult to implement without trusted third parties managing it, and that, as mentioned above, networks of peer to peer nodes were vulnerable to 33% collusion attacks.
B-money
Following Bit Gold, B-money [20] was a parallel proposal a little bit later in 1998 by Wei Dai [21], another cypherpunk. In addition to the cryptocurrency, it included a basic form of smart contracts.
The model also integrated a network of nodes that maintained a distributed ledger, with accounts and balances, and participants who performed work on their computers to show they had incurred in a significant computational cost to create the currency.
This currency would be valued according to current prices in the market of computational power, and the network of nodes would credit the account of the creator with their new balance.
The second part of B-money added the figure of escrow agents to guarantee transactions between network participants when they wanted to enter into smart contracts.
It is possible that B-money did not take off at the time because of the lack of detail on how to implement the different parts proposed, and because the network of nodes maintaining the ledger was also vulnerable to the 33% fault tolerance mentioned before.
RPOW
RPOW [22] stands for Reusable Proofs of Work and was created in 2004 by Hal Finney [23], yet another cypherpunk. The model of RPOW had a different approach as an attempt to solve the historic Byzantine fault tolerance problem: Participants would create their own proofs of work, as in Bit Gold, but they would transfer them directly to other users by a messaging system, rather than using a network of peer to peer nodes to maintain a property ledger.
At the center of this system was a verification server where, as participants transferred RPOWs from user to user, the new transactions needed new proofs of work, and the central server would only have the role of verifying that the proofs were genuine.
Although the system enabled the transfer of value from user to user directly, solving the Byzantine fault tolerance problem in that format, it had the drawdown that the centralized verification server, even if it was managed by a group of separate verifiers, still posed a risk of centralization as such verifiers had to be trusted for that function.
The Arrival of Bitcoin
As seen above, all the precursor systems always had some sort of vulnerability. Be it that they depended on central servers or trusted third parties, or that the consensus mechanism of the property ledger was vulnerable to collusion by sub-groups of participating nodes.
With the launch of Bitcoin [24] in 2009, the brilliant invention by Satoshi Nakamoto [25], that made it revolutionary, was what is called today the Nakamoto Consensus [26], which largely advanced in solving or significantly improving on these problems by integrating all the parts in a way that each one reinforced the other.
In the Nakamoto Consensus, all the nodes in the peer to peer network send all new transactions to all other nodes; then, they all use those transactions, plus the information of the previous block and a timestamp, as the puzzle for the next proof of work, based on a minimal difficulty threshold; when any of the nodes reaches a certain result based on the threshold, it broadcasts the result to all other nodes; when all other nodes receive the proof of work, they verify it according to the system’s algorithm and the chain of proofs they hold in their copies of the ledger; when the proof of work is verified, all the nodes credit the account of the node who solved the puzzle first with a number of tokens according to the Bitcoin monetary policy [27].
In this way, Bitcoin guarantees the value of the token, not only by the scarcity imposed by the monetary policy, but also because, to create new tokens, a large amount of computational work is needed.
This amount of computational work is also a key to solving the 33% vulnerability of peer to peer networks mentioned before. As the minimal difficulty threshold imposed by the Bitcoin algorithm implies that all the participating nodes have to spend, on average, ten minutes solving the puzzle, when any of the nodes discovers and sends the results, as it took more or less ten minutes, that guarantees to the rest of the network that all the other participants worked to solve the puzzle as well [28].
However, if anyone achieves more than 50% of computational power in the network, they can still, indeed, outrun the other nodes in producing blocks, potentially tampering with the property ledger. This is what is commonly called a 51% attack.
Therefore, the Nakamoto Consensus improvement is that it elevated the previous 33% consensus security threshold to 50%, meaning that any group of colluding nodes, to tamper with the property ledger, now needs more than 50% of the computing power in the system to do so.
In this way, Bitcoin has become the first successful [29], widely used form of purely digital money, resembling digital gold. However, the next step, smart contracts, is something it could not accomplish because of its internal design and limitations [30].
Smart Contracts on Ethereum
Where Bitcoin is called a pocket calculator, Ethereum is called a computer.
Ethereum [31], created by Vitalik Buterin [32] in 2015, uses the same base as Bitcoin; that is to say Nakamoto Consensus, plus a distributed property ledger, and a token as the monetary unit; but added a virtual machine [33] and a programming language to enable the programmability of the currency.
In other words, it enabled smart contracts.
The way it works is that it uses proof of work to create blocks with transactions that all the nodes in the network verify, but the ledger not only records accounts and balances, but also stores programs which become decentralized when they are added to the network.
These programs, like any software, can establish rules and conditions for executing transactions that transfer value across the network globally.
For example a simple program on Ethereum could be:
– if account X has $Y balance
– and if today is December 31st, 2021
– then transfer 5 coins to account Z
– if not, don’t do anything
This possibility of integrating decentralized programs has enabled decentralized applications or Dapps [34], which can run on these systems and have the same security features of blockchains.
Proof of Stake
As cryptocurrencies are open source public systems, they can be copied and implemented with changes as entirely separate systems. One of the changes many entrepreneurs and computer scientists had been wanting to implement was to migrate away from proof of work as the core value and security system of their cryptocurrencies.
The criticism of proof of work is that it uses a lot of energy [35] and that this is not good for the environment. However, Bitcoin has reached enormous scale at a global level [36], and more or less 77% of the system runs on renewable energy [37]. In fact, as renewables are cheaper, Bitcoin has actually accelerated the migration to them in many regions [38] [39].
Nevertheless, many new networks have been launched, using the Bitcoin and Ethereum models as their starting points, but with some new features and modifications, such as proof of stake [40] as their consensus mechanism. Other features they have added are voting systems for making decisions, treasuries as funding sources, and fragmentation of the ledger, in what is called sharding, to increase performance.
Examples of such networks are Polkadot, Cardano, EOS, TRON, and Tezos. All these systems may be found on CoinMarketCaps.com [41].
Even Ethereum is migrating to a proof of stake system [42].
Proof of stake replaces the need for computational work, thus reducing the energy expenditure, with security deposits by node operators. This security deposit is made in the system’s currency and is called a stake.
All nodes that have deposited a stake have the right to gather transactions and post them in the distributed ledger. After posting transactions, which resemble blocks in the proof of work systems, these validators enter into a lottery where they can earn the rewards for the current block. This makes the monetary model very similar to proof of work systems as well.
Even if proof of stake systems have been described as less secure by this author [43] [44], they do present a tradeoff in the form of scalability. Proof of work systems are more secure but less scalable in terms of transaction volumes, and proof of stake systems are less secure but much more scalable.
This apparent complementarity is why there is a real possibility that, eventually, these technologies will actually be integrated together into larger, more scalable and secure systems in the future [45].
What Are Not Cryptocurrencies?
The second most important thing to know when learning about cryptocurrencies is what are not cryptocurrencies.
Proof of work and proof of stake systems qualify as cryptocurrencies because their ultimate goal, however different their approaches may be, is to minimize the trust needed in third parties.
Trusted third parties are security holes because they hold people’s money and wealth, their personal data, manage everything on centralized servers, and they can be hacked or they can commit outright fraud [46]. In other words, they do not guarantee immutability [47] of the property ledger, balances, transactions, and smart contracts.
If the above is the case, then, by definition, currencies that are created and managed by centrals banks, or so called Central Bank Digital Currencies (CBDC) [48], are not cryptocurrencies, even if they mimic all the motions.
Private money schemes are also not cryptocurrencies. These include systems such as Facebook’s Diem (previously known as Libra) [49] and the so called stablecoins [50]; such as Tether, USD Coin, and DAI, amongst others; as they only import to the system the flaws and risks of financial institutions, central banking, and government sponsored fiat money that cypherpunks were trying to avoid in the first place [51].
References and Notes
[1] The Crypto Anarchist Manifesto – by Tim C. May: https://www.activism.net/cypherpunk/crypto-anarchy.html
[2] Cypherpunk – by Wikipedia: https://en.wikipedia.org/wiki/Cypherpunk
[3] Crypto Rebels – by Steven Levi – Wired Magazine: https://archive.is/5FPsA
[4] A Cypherpunk’s Manifesto – by Eric Hughes: https://archive.is/Cr7LH
[5] Shelling Out: The Origins of Money – by Nick Szabo: https://nakamotoinstitute.org/shelling-out/
[6] Smart Contracts – by Nick Szabo: https://archive.is/zQ1p8
[7] Trusted Third Parties are Security Holes – by Nick Szabo: https://nakamotoinstitute.org/trusted-third-parties/
[8] Satoshi Nakamoto Mentioned Trust Minimization 14 Times in the Bitcoin White Paper – by Donald McIntyre: https://etherplan.com/2020/02/29/satoshi-nakamoto-mentioned-trust-minimization-14-times-in-the-bitcoin-white-paper/10210/
[9] DigiCash – by Wikipedia: https://en.wikipedia.org/wiki/DigiCash
[10] David Chaum – by Wikipedia: https://en.wikipedia.org/wiki/David_Chaum
[11] Blind signature – by Wikipedia: https://en.wikipedia.org/wiki/Blind_signature
[12] HashCash – by Wikipedia: https://en.wikipedia.org/wiki/Hashcash
[13] Adam Back – by Wikipedia: https://en.wikipedia.org/wiki/Adam_Back
[14] Proof of work – by Bitcoin.it: https://en.bitcoin.it/wiki/Proof_of_work
[15] Bit Gold – by Nick Szabo: http://unenumerated.blogspot.com/2005/12/bit-gold.html
[16] Nick Szabo – by Wikipedia: https://en.wikipedia.org/wiki/Nick_Szabo
[17] Distributed ledger – by Wikipedia: https://en.wikipedia.org/wiki/Distributed_ledger
[18] Secure Property Titles with Owner Authority – by Nick Szabo: https://nakamotoinstitute.org/secure-property-titles/
[19] Byzantine fault – by Wikipedia: https://en.wikipedia.org/wiki/Byzantine_fault
[20] B-money – by Wei Dai: http://www.weidai.com/bmoney.txt
[21] Wei Dai – by Wikipedia: https://en.wikipedia.org/wiki/Wei_Dai
[22] RPOW – Reusable Proofs of Work – by Hal Finney: http://web.archive.org/web/20040815031415/http://rpow.net/
[23] Hal Finney – by Wikipedia: https://en.wikipedia.org/wiki/Hal_Finney_(computer_scientist)
[24] Bitcoin – by Satoshi Nakamoto: https://bitcoin.org/bitcoin.pdf
[25] Satoshi Nakamoto – by Wikipedia: https://en.wikipedia.org/wiki/Satoshi_Nakamoto
[26] Why Proof of Work Based Nakamoto Consensus is Secure and Complete – by Donald McIntyre: https://etherplan.com/2020/03/21/why-proof-of-work-based-nakamoto-consensus-is-secure-and-complete/10509/
[27] Bitcoin controlled supply – by Bitcoin.it: https://en.bitcoin.it/wiki/Controlled_supply
[28] Cryptography Mailing List – Bitcoin P2P e-cash paper – by Satoshi Nakamoto:
“The proof-of-work chain is a solution to the Byzantine Generals’ Problem. I’ll try to rephrase it in that context.”
Source: https://satoshi.nakamotoinstitute.org/emails/cryptography/11/
[29] Money, Blockchains, and Social Scalability – by Nick Szabo: http://unenumerated.blogspot.com/2017/02/money-blockchains-and-social-scalability.html
[30] The dawn of trustworthy computing – by Nick Szabo: https://unenumerated.blogspot.com/2014/12/the-dawn-of-trustworthy-computing.html
[31] Ethereum – by Wikipedia: https://en.wikipedia.org/wiki/Ethereum
[32] Vitalik Buterin – by Wikipedia: https://en.wikipedia.org/wiki/Vitalik_Buterin
[33] What is Ethereum in Layman’s Terms? – by Donald McIntyre: https://etherplan.com/2017/01/25/what-is-ethereum-in-laymans-terms/6105/
[34] Decentralized application – Dapp – by Wikipedia: https://en.wikipedia.org/wiki/Decentralized_application
[35] A proof of stake design philosophy – by Vitalik Buterin: https://medium.com/@VitalikButerin/a-proof-of-stake-design-philosophy-506585978d51
[36] Bitcoin nodes map – by Bitnodes: https://bitnodes.io/
[37] The Bitcoin Mining Network – Trends, Composition, Marginal Creation Cost, Electricity Consumption & Sources – by Christopher Bendiksen, Samuel Gibbons, and Eugene Lim: http://etherplan.com/bitcoin-mining-network-november-2018.pdf
[38] Canadian Province Offers Low-Cost Energy Incentives To Bitcoin Miners – by Jessie Willms – Bitcoin Magazine, April 2019: https://bitcoinmagazine.com/articles/canadian-province-offers-low-cost-energy-incentives-bitcoin-miners
[39] Bitcoin Miners in Nordic Region Get a Boost From Cheap Power – by Jesper Starn – on Bloomberg:
“The main environmental benefit from basing the mining in the Nordic region is that the electricity is almost carbon-free, consisting mostly of hydro, nuclear and wind power. That is becoming increasingly important for the many institutional investors attracted to crypto-currencies and one of the main factors behind the latest price surge. Having coin flowing from the Nordic region helps reduce the political risk profile of Bitcoin.”
Source: https://archive.is/otSLV#selection-3313.0-3313.12
[40] Proof of stake – by Wikipedia: https://en.wikipedia.org/wiki/Proof_of_stake
[41] CoinMarketCaps: https://coinmarketcap.com/
[42] Ethereum Classic vs Ethereum 2.0, What is the Difference? – by Donald McIntyre: https://etherplan.com/2019/07/23/ethereum-classic-vs-ethereum-2-0-what-is-the-difference/8425/
[43] Proof of Work has Division of Power, Proof of Stake Does Not – by Donald McIntyre: https://etherplan.com/2019/05/18/proof-of-work-has-division-of-power-proof-of-stake-does-not/7619/
[44] Why Proof of Stake is Less Secure Than Proof of Work – by Donald McIntyre: https://etherplan.com/2019/10/07/why-proof-of-stake-is-less-secure-than-proof-of-work/9077/
[45] Model for an Ethereum and Ethereum Classic Collaboration – by Donald McIntyre: https://etherplan.com/2019/05/17/model-for-an-ethereum-and-ethereum-classic-collaboration/7594/
[46] 10 Blockchain Principles for Blockchain Governance – by Donald McIntyre: https://etherplan.com/2018/03/20/10-principles-for-blockchain-governance/6803/
[47] The Meaning of Blockchain Immutability – by Donald McIntyre: https://etherplan.com/2018/04/19/the-meaning-of-blockchain-immutability/6852/
[48] Central Bank Digital Currencies (CBDC) – by Investopedia: https://www.investopedia.com/terms/c/central-bank-digital-currency-cbdc.asp
[49] Diem (originally, Facebook’s Libra) – white paper: https://www.diem.com/en-us/white-paper/
[50] Stablecoins – by Wikipedia: https://en.wikipedia.org/wiki/Stablecoin
[51] From Gold to Fiat to Bit Gold to Bitcoin – by Donald McIntyre: https://etherplan.com/2020/04/25/from-gold-to-fiat-to-bit-gold-to-bitcoin/11352/
Code Is Law