You can listen to or watch this video here:
A proof of work (PoW) based Nakamoto consensus blockchain as Ethereum Classic (ETC) is a subjective system of accounts, balances, and smart contracts, anchored on top of an objective physical base that uses large amounts of energy to produce blocks of data, which are subsequently added to a highly secure chain of blocks in the system. By making this anchoring, the subjective layer acquires orders of magnitude more objectivity, thus security, than if it were not connected to a proof of work physical base.
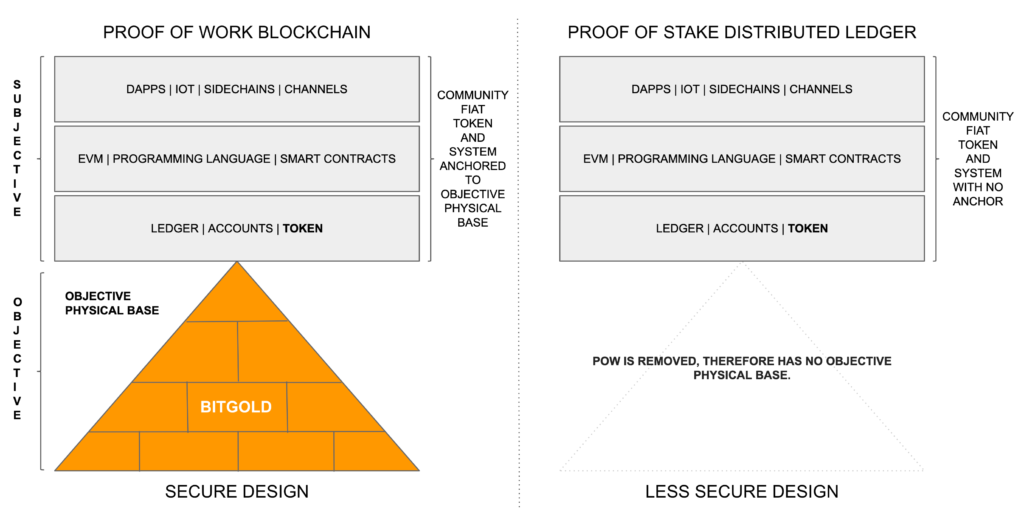
In search of scalability, proof of stake (PoS) systems remove the computationally unscalable proof of work physical base, making their systems highly subjective again.
Because of the above, I think the correct name of proof of stake systems is “proof of stake distributed ledgers” as they are not systems that expend large amounts of energy to build and secure blocks of data. In fact, the reason they create batches of transaction data and link them as if they were “blockchains” is just an appeal to authority by mimicking real blockchain design, but that serves no purpose in increasing or decreasing objectivity, thus security, in the distributed ledgers.
What I call the “subjective” section in these systems, shared by both blockchains and distributed ledgers, is basically where the useful features and functionality reside.
As seen in the diagram above, the components of the subjective section are the ledger, with accounts and balances of the native token, the EVM (Ethereum Virtual Machine) when applicable, a programming language, and smart contracts. On top of these go the decentralized applications (DAPPs), other applications such as IoT, and higher level scaling solutions such as channels and sidechains.
I call the subjective section in blockchains and distributed ledgers a “community fiat token and system” as an analogy to fiat monetary systems, but instead of managed by governments or central banks they are managed by their ecosystems. In other words, all the rules, balances, smart contracts, and applications can be changed if agreed upon by the participants.
However, the brilliant invention by Satoshi Nakamoto was to anchor these subjective, thus insecure systems, to an objective physical base. Without that anchor, proof of stake distributed ledgers basically become traditional subjectively managed systems again.
It doesn’t matter what complex designs and choices they do, for example, federations, elected block producers, rotating validators, bakers, pools, epochs, slots, voting, quadratic voting, liquid democracy, slashing, treasuries, or any combination thereof, because in the end, it all depends on subjective human incentives, not on any other form of objective security.
Summary of Features and Differences
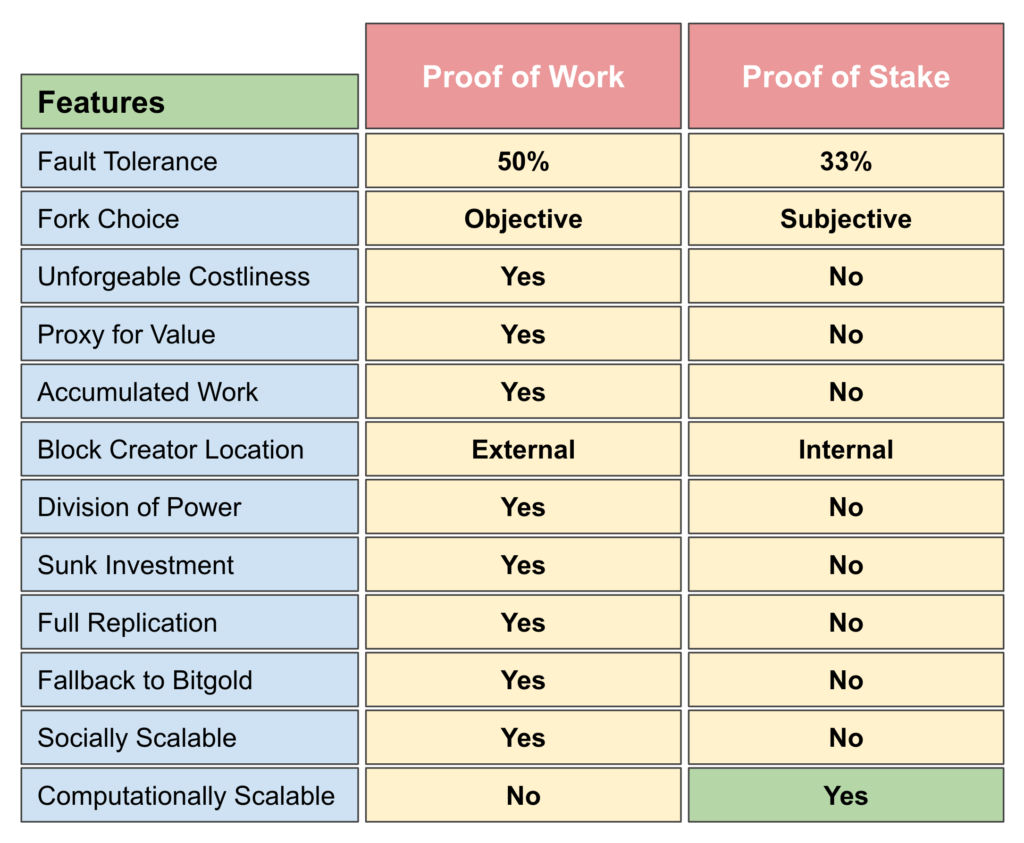
To illustrate why a PoW objective anchor is more secure than PoS, it is worth reviewing the differences between the systems on a feature by feature basis:
Fault Tolerance
Fault tolerance is the number of nodes in a distributed network who can disrupt the system if they are dishonest by sending corrupt information to their peers. Before Bitcoin, distributed systems achieved 33% fault tolerance. PoW, introduced by Bitcoin, has a fault tolerance of 50%. It is worth mentioning Bitcoin did not really solve the standard fault tolerance problem to achieve this level of security, but really bypassed it by creating an external physical signal miners send to the nodes in the network.
PoS, by removing PoW, remains a 33% fault tolerance system.
Fork Choice
The fork choice is the decision rule network participants have to use when presented with more than one chain when it splits, when they join for the first time, or when they leave and join again. As an external physical signal, PoW enables a clear objective fork choice in the form of the “longest proof of work chain“. It is objective because only with the computing power of the whole network is that the longest chain can be established.
As PoS systems don’t count with such an objective quantity to decide the correct chain, they have to use a subjective decision making process by the participants. This means they need to consult offchain with block explorers, developers, miners or other sources to be able to decide what chain to follow. This applies, in case of splits, to participating nodes in the network, new entrants, and nodes who leave and join again.
Unforgeable Costliness
One of the basic physical features of sound money is that it is very costly to produce to guarantee it can’t be forged. PoW provides this costliness of the tokens as miners incur in huge costs, in data centers and electricity, to be able to build blocks. This makes PoW tokens, as $ETC and $BTC, unforgeable in practice.
In PoS systems, because the database with accounts and balances is trivial to write by nodes and stakers in the system, there is no objective costliness.
Proxy for Value
The costliness in PoW mentioned in the point above also serves as a proxy for the value of the tokens in the broader economy.
In PoS systems this feature is not present, so their tokens have no objective measure of value.
Accumulated Work
As miners in PoW blockchains do work on a block by block basis, that work is not only a barrier for dishonest nodes to tamper with the current or latest blocks, but that work actually accumulates as the chain is built. This means blocks that are buried further away in the chain become exponentially more difficult for attackers to change or forge. For example, at the time of this writing, it would take 340 days with 100% of the current hashing power in the Bitcoin network to be able to reverse the entire chain.
In PoS distributed ledgers, because they don’t use PoW, to reverse the entire chain is trivial in terms of computational work, so it can be done in a few minutes.
Block Creator Location
As mentioned above, in PoW, mining is an external process to the network of nodes who hold the ledger with accounts, balances, and smart contracts. This separates the ledger from the block creators which gives the network of full nodes several benefits of security in their independence.
In PoS, as the stakers can only participate if they actually have deposits in the ledger, that makes them internal to the database, therefore all the other nodes in the network, who maintain the ledger, cannot be independent from block creators.
Division of Power
The previous point is extremely important in terms of security because, in PoW, full node operators, who also maintain the ledger, can delink from block creators if they become corrupt or dysfunctional to the network. In PoS systems, that is impossible, they are stuck with the stakers, making the distributed ledger not censorship resistant.
Sunk Investment
In PoW systems, miners have real “stake” in the system as they actually use capital to buy very costly equipment, build data centers, and buy electricity to produce blocks. This means that once they sink capital, the only way to recover it is to actually mine on the chain to be able to recover it with a profit.
In PoS systems, stakers are actually not “stakers” because they sink no capital, nor convert capital into any form of risky investment. They just move cash from a bank into a distributed ledger and continue earning interest for a trivial activity. Cash is not “investment” it is just uninvested capital that is running no risk whatsoever.
Full Replication
The other fundamental security design of secure blockchains is the full replication of the database. This means that the ledger is more secure as it is copied in as many nodes globally in the network as possible.
Several proof of stake networks, such as Ethereum 2.0 and Cardano, in their search for higher scalability, are migrating from a replicated format to a fragmented database through sharding. This strategy further reduces security in those distributed ledgers.
Fallback to Bitgold
As it is illustrated in the first image in this article above, proof of work based systems are a variation of a system created by Nick Szabo called Bitgold. That system uses proof of work to have unforgeable costliness to produce “digital gold” in the system and does not have an arbitrarily determined token as ETC or BTC. It can be said that PoW blockchains are Bitgold, but with a ledger, token, and the other components on top. This is important because if the fee system in these networks happens to fail as a compensation mechanism for miners, or if the ecosystem, however unlikely, decides to modify the monetary policy to issue more tokens irresponsibly, then these systems can fall back and convert their tokens into Bitgold, and continue building digital gold perpetually as was the original design.
PoS systems, by eliminating the PoW physical base have entirely discarded this possibility.
Socially Scalable
Social scalability is determined by the fact a system is objective so that no one can be excluded from participating or using the system for any human condition or bias. As PoW blockchains are highly objective, they are socially scalable on a planetary scale.
PoS systems will likely evolve to have very few stakers who control the system in practice. Those stakers will be easily identifiable and will be either pressured, or, by personal or institutional conviction, will have a bias to exclude participants due to their origin, identity, activities, nationality, or other conditions, just like traditional systems do today.
As PoS systems are subjective, which is the basis for a lack of social scalability, they will be confined and restricted to certain segments or regions, very similar to traditional systems today.
Computationally Scalable
This is the main feature that makes PoW less performant, and PoS systems very useful perhaps in combination with PoW systems. As PoW requires a lot of work in the form of computations, their blocks can only be created every 15 seconds to 10 minutes. They also have some other physical restrictions in terms of local processing and global propagation, this makes PoW computationally unscalable as compared to PoS.
The Six Proof of Stake Fallacies
Given the above comparisons of the two systems, but the public narratives that proof of stake proponents have made popular, there are six PoS fallacies that need to be clarified and debunked:
1. The “sleeping with the enemy is fine” fallacy
Mining in PoW is external, but stakers in PoS are inside the ledger. In other words, full nodes cannot get rid of stakers in PoS systems, even if they split. This means PoS is not censorship resistant as censors cannot be evicted. Sleeping with the enemy is not fine.
2. The “staking is sunk investment” fallacy
There is really no such thing as “staking” in PoS, it’s just a group of trusted rich participants controlling the system. Miners are, in fact, real stakers because they do sink capital in equipment, data centers, and electricity, and can only recover their investments after mining for months if not years.
3. The “computer science innovation” fallacy
PoS is just a community fiat system, or subjective traditional governance system. There is no innovation whatsoever, and no computer science breakthrough in any way. In fact, the central banking model is, in practice, a proof of stake system: Participating banks have to make security deposits, have minimal capital requirements, and follow the rules to be licensed to accept and process transactions, maintaining the account balances of their customers. PoS is no different.
4. The “distributed ledger is blockchain” fallacy
PoS networks mimic the structure and processes of real blockchains as an appeal to authority, but are just distributed ledger networks, they are not blockchains. Blockchains are systems with expensive machines and energy investment to do incredible computing in proof of work to build very costly blocks. PoS networks are trivial and cheap to run.
5. The “mathematical gimmicks” fallacy
Many PoS projects design highly complex mathematical models and algorithms to compensate for the lack of security of their systems, giving the impression of and appealing to high academic prowess, but just hiding centralization, and gaining nothing in marginal security other than the base standard Byzantine Fault Tolerance of 33%.
6. The “voting gimmicks” fallacy
Many PoS projects invent voting mechanisms, to compensate for their insecure models, by appealing to the authority of “democracy”, “balance of power”, and “basic guarantees” in traditional systems. But that is no innovation and is insecure. True blockchains seek precisely to avoid those systems and decision making processes in the first place. “Voting” is the worst mechanism to make technical decisions in blockchains, it is just a conflict minimization device, but does not guarantee in any way permissionlessness nor sound engineering choices. And, conflict is actually good in blockchain ungovernance systems.
Conclusion
There are many reasons why PoS is less secure than PoW, very likely many more reasons than explained in this article. Furthermore, PoS systems should be better called “non-proof-of-work distributed ledgers” because they don’t even have true staking in the system.
However, PoS is better than traditional systems as they have some additional levels of distribution of power and are more diverse jurisdictionally. It could be said, they lie somewhere in the middle, in terms of security and social scalability, between PoW and traditional fiat systems, but much closer to fiat systems than to PoW.
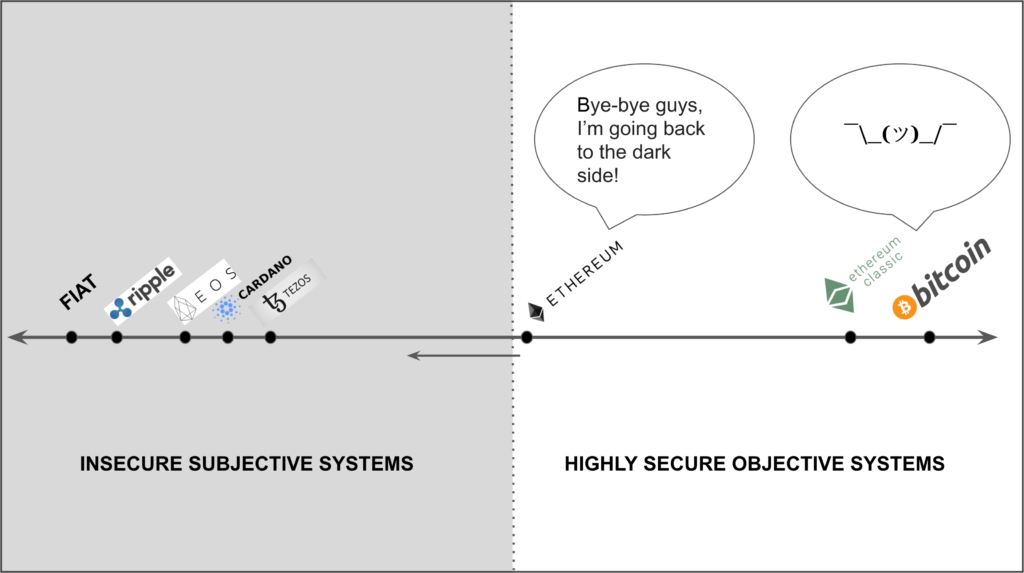
If PoW based blockchains are combined subjective and objective systems, this model could actually be extended to PoS distributed ledgers, which could be anchored to existing PoW blockchains to gain higher levels of security.
I want to thank @hugohanoi, @StopAndDecrypt, @nic__carter, @eric_lombrozo, @pyskell, and @evoskuil for their writings in the last three years, the twitter discussions, and their feedback which helped define the assumptions for this article.
Code Is Law