You can listen to or watch this article here:
In a previous article I wrote why proof of stake is less secure than proof of work. In this article I am going to explain why the proof of work consensus mechanism, or better named Nakamoto consensus, invented by Satoshi Nakamoto for the Bitcoin network, is secure and complete.
To explain the mechanism I am going to describe the proof of work algorithm or process first, explain how it works in the Nakamoto consensus, why it is secure and complete, and finally how it benefits money, property and agreements on blockchains such as Bitcoin and Ethereum Classic.
What Is Proof of Work?
To explain what is proof of work, it is necessary to explain what is “hashing” first. A hashing algorithm is a function that turns an arbitrary string of data, such as another number or a love letter or a list of transactions, into a number with a fixed length.
For example, the text “hello”, using the hash function SHA-256, produces the hash:
2cf24dba5fb0a30e26e83b2ac5b9e29e1b161e5c1fa7425e73043362938b9824
The proof of work process per se in a network like Bitcoin starts with a group of 4 numbers, then hashing them by iterating a nonce multiple times until a target “difficulty” is hit. Then, the miner who hits the target first wins the rewards.
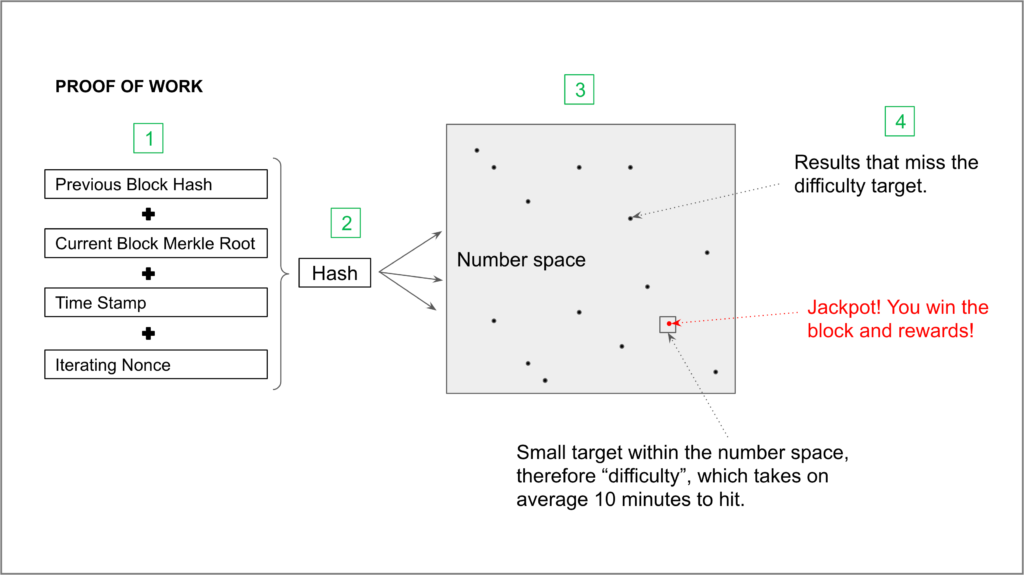
The steps in the proof of work process in the diagram above are:
1. Data to hash
The 4 numbers that are hashed to create a new block are the hash of the previous block, so a chain of related hashes can be built, hence “blockchain”; a hash, called Merkle root, containing all the transactions of the current block; a time stamp; and an arbitrary nonce, which is the number that is iterated in the next step to find a hash within the difficulty target.
2. Iterated hashing
If the four numbers were simply hashed, they would result in a single hash, but, to try many times, in fact billions or trillions of times per second, to hit the difficulty target, the nonce is iterated constantly to increase the chance that one of the resulting hashes hits it.
This step is the one that constitutes the “work” in proof of work, which is the most critical aspect of Nakamoto consensus, because all miners collectively spend a large amount of energy every ten minutes, on average, working to find a hash within the difficulty target.
3. Hitting the Difficulty target
All the numbers or hashes possible that a function as SHA-256, which is the one used by the Bitcoin network, can generate from arbitrary strings of data, such as lists of Bitcoin transactions, is incredibly large, something like 2^256, which is perhaps more numbers as are atoms in the universe.
The difficulty target consists of determining a small range of numbers that can be used for the current block. As an example, if the whole number space were from 0 to 10, but the difficulty target were set at 3 or below, that means that the miners have to hash several times the first three numbers with an iterated nonce until the resulting hash is 3 or below.
So, if they do the hash and the result is 8, that one is discarded. If after several tries they find a hash that is 2, then the miner who found it hit the jackpot! This means they win the rewards for that block, as per the Nakamoto consensus, if they were the first ones to find and propagate it to the network.
4. Block Finalization and Rewards
Once a miner finds a hash within the difficulty target, they have to finalize the block by entering a public key with a balance representing the current miner rewards for that block and send it to the full nodes of the network for verification and inclusion in the blockchain. Once included in the blockchain, the miner can rest assured it has earned such rewards.
What Is Nakamoto Consensus?
As may be seen in the diagram below, mining, therefore proof of work, is a component of the Nakamoto consensus.
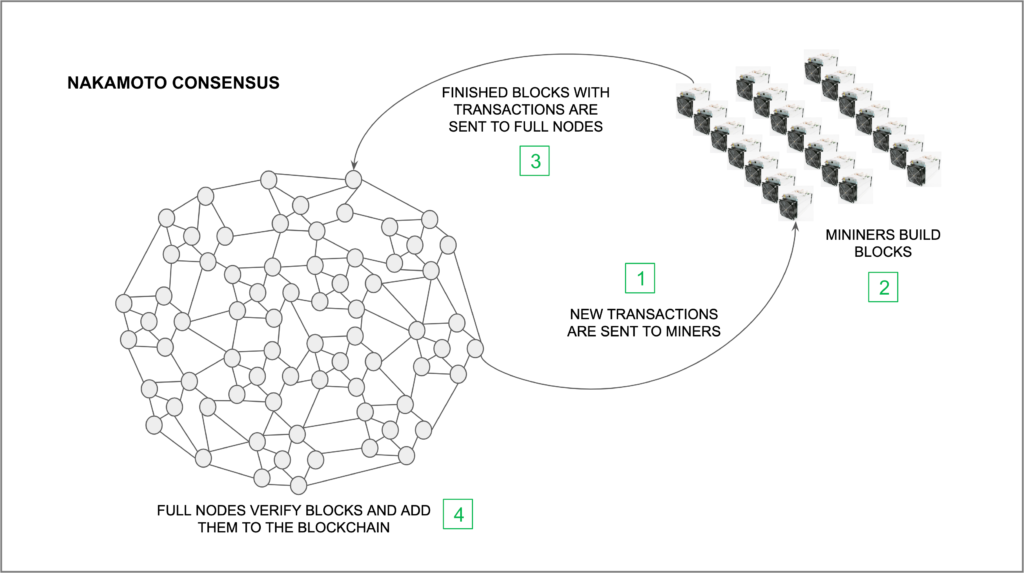
The steps in the Nakamoto consensus are:
1. Transactions are Gathered and sent to miners
As individuals, exchanges, wallet services, investors, and all other kinds of users and node operators send transactions to the network through full nodes, all transactions are sent to all other nodes in the network, to ensure full replication, including miners.
2. Miners Build Blocks
When miners receive transactions they group them and start the proof of work process described above. All miner computing power is deployed to find a hash that hits the difficulty target. When miners find a hash within the target, they finalize the block so it can be sent to the rest of the network.
3. Finished Blocks are Sent Back to Full Nodes
When a miner finds and finalizes a winning block it is immediately sent to the rest of the network so it is propagated and all full nodes can receive it.
Sometimes more than one miner will find a hash within the difficulty target. When this happens the network will select the one that was found first, or, if both blocks were found at the same time, they will work on both until one or the other becomes part of the longest chain.
4. Full Nodes Verify Blocks and add Them to the Blockchain
When full nodes receive new blocks, they verify that all transactions are valid, that the hash is correct, and the proof of work process was followed.
After verification, the block is added to the blockchain as the highest block, which adds to the quantity of computing work in the network since genesis. This means that all the computing power since genesis is accumulated creating a wall of protection for the blockchain.
As described in the previous section, when full nodes include a block in the blockchain, that also finalizes the payment of rewards to the winning miner. The rewards per block are the key economic incentive for miners in the Nakamoto consensus to participate and secure the blockchain.
The rewards are set by the network’s monetary policy, but also include the transaction fees that were sent together with transactions to incentivize miners to include them in the block. In the future, when monetary policy rewards diminish, the transactions fees will become the major part of miner payments.
Why Is Proof of Work Based Nakamoto Consensus Secure and Complete?
The way proof of work works in the Nakamoto consensus mechanism has a series of advantages that make it secure and complete because, together, they cover all the needs of safety, availability, and consistency of the system.

These advantages of proof of work based Nakamoto consensus are:
1. Proof ALL Computing Power HAs Participated
Nakamoto consensus provides proof that the great majority of computing power participates in building blocks. This is because, for any give block, at a certain difficulty, that miners in the network took more or less 10 minutes to hash it is physical evidence that the great majority of computing power participated in building that block.
The above is Satoshi Nakamoto’s famous solution to the Byzantine General’s Problem.
2. Chain Selection Point for Permissionless Exit and Entry and unification in case of chain split
If the blockchain is most valuable and secure when all miners and nodes are working on the same identical chain globally, how do they all coordinate on a single point with no central authority or third party directing them?
Nakamoto consensus solves this by providing a single chain selection point, or fork choice, which is a focal point for exiting and entering the network or, in case of chain splits, for the network to return to full consensus on a unified chain.
This is done by establishing the “longest chain rule” which means that all nodes and miners are programmed to always work on the chain of blocks that has the most proof of work done on it since genesis. This objective focal point for all participants, which is automated in the software clients of the network, is critical to eliminate the need for trusted third parties, based on subjective judgement, to serve as arbiters and directors of the system.
Additionally, this objective fork choice also minimizes Sybil attacks because, as long as a node is connected to at least one honest node, it is easy to always select the best version of the chain.
3. A Security Barrier Against Attackers
Proof of work based consensus is a security barrier against attackers in both the present processing of transactions and for all past transactions. In the present, it is a barrier for attackers to double spend in the current block as they would need more than 50% of the mining computing power just to enter a second transaction to eliminate the first one.
As to all past transactions, it is the same concept, but, as the proof of work is cumulative, at this point it would take hundreds of days to reverse older blocks. In fact, at the time of this writing, it would take more or less 400 days, with 100% of the current hashing power, to reverse the Bitcoin chain since genesis.
4. Digital Scarcity Through Unforgeable Costliness
As explained by Nick Szabo in his seminal paper Schelling Out: The Origins of Money, unforgeable costliness is the concept that a form of sound money must be not only durable, transferable, portable, divisible, and fungible, but also costly to create.
This costliness guarantees that it is not easy for others to forge or create large copies of the currency, thus diluting its value. In other words, as proof of work is very expensive because it requires large amounts of computation, thus energy spending, it enables digital scarcity through the sheer cost and work that it requires, hence, unforgeable costliness.
5. A Proxy for Value In the Economy
The same costliness that guarantees scarcity, also serves as a proxy for value for the native currency in the economy. Even though value is individual and subjective, a transparent proxy for value as proof of work helps accelerate price discovery reducing transaction costs, facilitating coordination in the market.
What Are the Benefits for Money, Property, and Agreements?
As seen in this article, the main benefits of proof of work based Nakamoto consensus, which combined make it secure and complete, are that it provides proof all computing power participated in building blocks, provides a focal point for exiting and entering the network and in case of chain splits, it is a cumulative security barrier against attackers, enables digital scarcity through unforgeable costliness, and it serves as a proxy for value in the economy.
For blockchains such as Bitcoin and Ethereum Classic, all these benefits are critical to secure their underlying native currencies, the consistent production of valid blocks, ordering of transactions, and the storage and protection of property and agreements in a trust minimized, immutable, and permissionless system on a global scale.
Code Is Law