Proof of work technology [1] is the key component in the Bitcoin [2] Nakamoto consensus mechanism [3]. It is a computing process that requires large amounts of computing power to prove that a lot of work has been done, and cost incurred, to reach a desired result.
In Bitcoin and in nature, proof that a high cost has been incurred is used to guarantee the quality and honesty of signals, so that the receivers of such signals can be reasonably convinced and assured that the senders are who they claim to be, or have the sought economic or biological benefits [4].
The Model
The model of proof of work or proof of cost that is widely observed in systems and in nature usually involves a signal sender and a signal receiver.
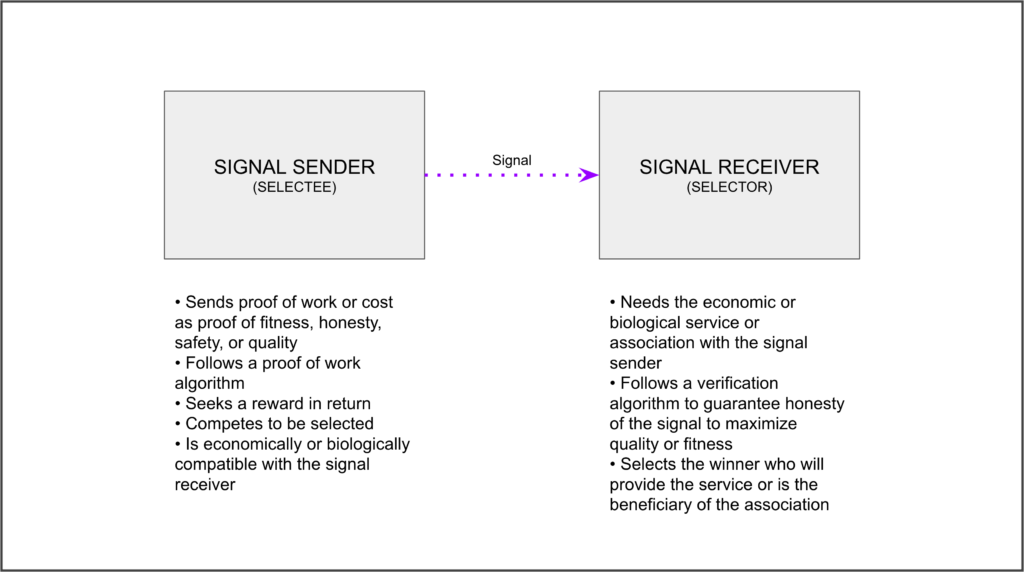
The signal sender, or selectee, is usually an entity or organism that is willing to incur in the high cost of proof of work in expectation of an even higher reward if the proof is accepted, thus the sender selected, by the signal receiver, or selector.
The signal receiver is usually an entity or organism that needs the service or to associate with the signal sender, but, to guarantee the quality and safety of such service or association, needs to verify that the potential provider is honest in its signaling, thus proving its fitness, legitimacy, and compatibility.
Usually, there is a competition between signal senders to be selected by signal receivers. Whoever wins and is selected by the signal receiver gets the reward, which can be some economic or biological benefit.
Proof of Work in Bitcoin
In Bitcoin the signal senders are the miners [5] [6], and the signal receivers are the node operators who store the database, also called the blockchain, with the transaction history, accounts, and balances [7].
Nodes need to secure the native currency of Bitcoin, the consistent production of valid blocks, and ordering of transactions. For this, miners compete for block rewards and fees to gather transactions, put them into blocks, and hash them using enormous amounts of energy [8] [9]. These blocks are then sent to node operators for verification.
This large expenditure of energy serves as a legitimate and honest signal to node operators that the most amount of work has been done to create the blocks with the ordered transactions, thus updating accounts and balances.
The proof of work mechanism within the Nakamoto consensus algorithm serves several purposes sought by node operators.
Consensus
As, given a certain computational difficulty provided by the algorithm, it must take around ten minutes for the whole network of miners to build a block, when a block is found by a miner, it is proof that the whole network [10], with all its hashing power, worked and invested energy and capital on it.
Chain Selection
As all miners contribute blocks to node operators, node operators go linking them in the database as a chain of blocks that increases the accumulated work as more blocks are added. The latest block every ten minutes, as it always has the most accumulated work, turns into a focal point for all participating, new incoming, and reentrant miners and node operators to join and leave the network permissionlessly [11].
A Digital Security Barrier
As all hashing power in Bitcoin from all participating miners is dedicated to compete to make blocks to get the block rewards and fees, it is very difficult, or practically impossible, for external attackers to start forging blocks, accounts, and balances and tricking node operators into accepting them into the blockchain [12] [13].
These benefits together guarantee to node operators and users of Bitcoin that they can count with the consistency, decentralization, integrity, and permissionlessness of the network and the blockchain in the long term on a global scale [14].
Proof of Work in Nature
The Physics of Gold
Gold is really a case of proof of work alone, by itself, with no purposeful interactions between signal senders or receivers, but it does have a similar dynamic between nature and humans. This is because nature requires and uses a lot of energy to create gold, and humans use that information as an indication of its scarcity, thus usefulness as a monetary device, and even as a secondary display of fitness as jewelry, and other wealth signaling methods [15].
In fact, the way Bitcoin works is basically an imitation of how gold is created in nature [16] [17]. Gold atoms have an atomic number of 79 and an atomic weight of 197. This means that a fusion of 79 protons and 118 neutron needs to occur for one atom of gold to be forged.
With such numbers, the amount of energy needed to create gold exceeds the normal energy at the core of stars. So, gold is normally created in large events such as supernovae or when neutron stars collide [18].
The above makes gold very scarce, relative to other elements in the universe [19], but it is also scarce on earth because during the planet’s early history, when it was brought carried by meteorites, like other heavy metals, it tended to drift to the center of the earth. This makes gold scarce not only because it took a lot of work in the form of energy for its primary production, but it takes a lot of work and capital investment for humans to actually produce it out of minerals and mines on the earth’s crust [20].
Chemical Reactions
Similar to the physics of gold, chemical reactions don’t have actual conscious signal senders or receivers, but, in chemical bonds, there are also analogous interaction between atoms or molecules that require certain levels of energy to create bonds. The stronger the energy, the stronger the bonds [21].
For example, if two atoms of the same element are put together and form an electrostatic ionic bond, this is a weak kind of bond and they don’t form more stable structures like molecules.
However, if two atoms are submitted to higher levels of energy, they can get closer to form a covalent bond, in which they share pairs of electrons, and form molecules, which are stronger and more stable types of bonds.
Biology of Neurons
At the simplest level, living cells do form signaling relationships that depend on proof of quantities, which may be considered forms of work or cost.
For example, neuron cells store or transmit information only if a certain amount of stimuli is received through their dendrites from other neurons. When signaling presynaptic neurons send messages through their axons and synapses between cells, the receiving or postsynaptic neuron will activate a corresponding action potential toward other neurons, muscle, or gland cells only if a minimal threshold in voltage differential in the electrochemical gradient is reached [22] [23].
The same happens with memory between neurons, as pathways and receptors will be created, added, or strengthened only if certain interaction frequencies and intensities exist between them [24].
This model between cells and multicellular organisms, where the signaling algorithm requires a minimum stimulus threshold to warrant storing or transmitting information, is a form of proof of work, and must have evolved not only to overcome environmental noise, as in information theory [25] [26], but also to minimize cheating by other cellular and multicellular organisms.
Sexual Selection in Animals
In the case of mating strategies, in many animals the definitions of signal sender, signal receiver, and honest signaling fit very well.
For example, the peacock, in the peafowl species, is famous for displaying an incredibly costly tail of feathers with vibrant and attractive colors. This signaling strategy is designed to convince the very strict and selective peahens into mating with them.
The proof of work and cost in this kind of device is the fact that such plumage requires excellent and abundant feeding, health, and physical fitness by the peacock, it is very heavy and cumbersome to carry, and it poses an additional risk of being very overt and visible for predators to detect [27].
Another example is the North American moose. During the mating season, surging hormones in moose bulls makes them grow huge antlers. These large structures become a weight and a significant cost to grow and carry. The antlers are also used to engage in fierce fights against other males to compete for mating rights.
The moose cows are gathered by bulls who defend the group and try to impress them by displaying and fighting with other bulls. The females watch these fights and whoever is the winner is usually who they end up mating with. All through the season, several bulls may come to challenge the current group leader, and usually the winner takes the females [28].
The proof of work mechanism here consists in proving to females who is the strongest and fittest bull so that their potential offspring may be equally fit if a female, or may have higher chances of mating in the future if a male.
Selection of Leaders in Humans Based on Military Success
As humans are animals with more complex organizational structures, proof of work or honest signaling are used in several ways in addition to sexual selection. One of those ways is selection of leaders.
For example, the Roman legions used to declare their military generals and leaders “Imperator”, which meant “to lead” or “to command”, as a sort of honor, statement of loyalty, and affirmation of their authority, after they successfully led them to win battles or wars. As the military grew its influence in the Roman Republic, the term and custom eventually turned into a concrete political action, as Imperators eventually became real emperors starting implicitly with Caesar, but most explicitly with Augustus and onwards [29].
Later in the Roman Empire, it became practically a condition that proven and successful military leaders were the ones to become emperors [30].
The proof of work in this case may be interpreted as the proven skills in leading large amounts of men in concrete battles, with enormous investment or loss in life and treasure, to signal the fitness, effectiveness, and quality of leadership.
There are many examples in history of proof of work by signal senders, in the form of military success to guarantee leadership quality and effectiveness to signal receivers.
Some of these were Alexander the Great, through the conquests in north Africa, the Middle East, and Central Asia; Charlemagne, as the third generation of military leaders who, during his tenure, unified the Franks, the Germans, and parts of Italy to eventually form what would become the Holy Roman Empire; Napoleon, who proved his credentials by defending France, first as soldier and military leader, and then expanded the French Empire as Emperor of France; and, in modern times, Dwight D. Eisenhower, who led the invasion of Normandy in 1944-45 during World War II, which served as his signaling platform to become president of the United States for two terms starting in 1953.
Money Based on Unforgeable Costliness
Proof of work is very important as a feature of money because humans are attracted and need objects that are scarce, costly to create, durable, portable, divisible, fungible, and transferable.
The features that proof of work provides are scarcity through unforgeable costliness. This means that when an object requires a lot of work or cost to create, that usually correlates with its scarcity.
Scarcity, together with the other monetary features, is important because it is the only way for money to serve as a focal point, or medium of exchange, between untrusting individuals or groups [31].
If a form of money or object were easy and cheap to create, then it would be readily available in large quantities for all participants, rendering it useless as a medium of exchange, and even as a secondary proof of work and cost device.
As described earlier in this article, an example of a suitable proof of work form of money is gold. Other forms of money used in the past were certain species of shells, as they were costly to obtain, standardize, and shape into specific formats, for example beads; salt, as at certain times in history and specific regions it was a very scarce and costly commodity; and Rai stones in the island of Yap, which were quarried from the remote island of Palau [32].
Conclusion
The key of proof of work as a general honest signaling system is that there are senders competing for a reward and receivers selecting for the best options between senders. If the signaling format were not based on work or cost, it would be cheap to communicate any information, whether true or false.
In a competitive context, where fitness and honesty are economically or biologically critical, cheap signaling methods would make it impossible for receivers to judge what options are the best or more optimal for them.
It is worth noting that competition leads to natural hierarchies as innate differentials in abilities between competing signal senders will inexorably create ranks and classes between them [33].
If signal senders were not competing, then the best economic or biological benefits would not be produced.
References
[1] Proof of work – by Wikipedia: https://en.wikipedia.org/wiki/Proof_of_work
[2] Bitcoin: A Peer-to-Peer Electronic Cash System – by Satoshi Nakamoto: https://bitcoin.org/bitcoin.pdf
[3] Why Proof of Work Based Nakamoto Consensus is Secure and Complete – by Donald McIntyre: https://etherplan.com/2020/03/21/why-proof-of-work-based-nakamoto-consensus-is-secure-and-complete/10509/
[4] Signalling theory – by Wikipedia: https://en.wikipedia.org/wiki/Signalling_theory
[5] Mining – by Bitcoin Wiki: https://en.bitcoin.it/wiki/Mining
[6] Proof of Work has Division of Power, Proof of Stake Does Not – by Donald McIntyre: https://etherplan.com/2019/05/18/proof-of-work-has-division-of-power-proof-of-stake-does-not/7619/
[7] Blockchain – by Wikipedia: https://en.wikipedia.org/wiki/Blockchain
[8] Bitcoin network graphs – Total network hashing rate – by Sipa.be: http://bitcoin.sipa.be/
[9] Cambridge University Judge Business School – Bitcoin Electricity Consumption Index – Bitcoin Mining Map: https://cbeci.org/mining_map
[10] The proof-of-work chain is a solution to the Byzantine Generals’ Problem – by Satoshi Nakamoto – Cryptography Mailing List – Bitcoin P2P e-cash paper: https://satoshi.nakamotoinstitute.org/emails/cryptography/11/#selection-5.0-9.24
[11] Longest Chain – The chain of blocks that nodes adopt as their blockchain – by Greg Walker: https://learnmeabitcoin.com/technical/longest-chain
[12] Bitcoin Security Model: A Deep Dive – by Jameson Lopp: https://www.coindesk.com/bitcoins-security-model-deep-dive
[13] Bitcoin Miners Beware: Invalid Blocks Need Not Apply – Bitcoin is an impenetrable fortress of validation – by StopAndDecrypt – on Hackernoon: https://medium.com/hackernoon/bitcoin-miners-beware-invalid-blocks-need-not-apply-51c293ee278b
[14] Bitnodes – Global Bitcoin Nodes Distribution: https://bitnodes.io/
[15] Collecting metal: the inner and outer worlds of jewelry, coins, bullion bits, and odd shiny things – by Nick Szabo: http://unenumerated.blogspot.com/2017/03/collecting-metal-inner-and-outer-worlds.html
[16] Introduction to Cryptocurrencies – by Donald McIntyre: https://etherplan.com/2020/11/16/introduction-to-cryptocurrencies/13648/
[17] From Gold to Fiat to Bit Gold to Bitcoin – by Donald McIntyre: https://etherplan.com/2020/04/25/from-gold-to-fiat-to-bit-gold-to-bitcoin/11352/
[18] How Is Gold Formed? Origins and Process – Natural gold formed before the birth of the solar system – by Anne Marie Helmenstine, Ph.D. – ThoughtCo: https://www.thoughtco.com/how-is-gold-formed-4683984
[19] Abundance of the chemical elements – by Wikipedia: https://en.wikipedia.org/wiki/Abundance_of_the_chemical_elements
[20] About Gold – World Gold Council: https://www.gold.org/about-gold
[21] Chemical bond – by Wikipedia: https://en.wikipedia.org/wiki/Chemical_bond
[22] Action potential – by Wikipedia: https://en.wikipedia.org/wiki/Action_potential
[23] Summation (neurophysiology) by Wikipedia: https://en.wikipedia.org/wiki/Summation_(neurophysiology)
[24] Neuroplasticity – by Britannica: https://www.britannica.com/science/neuroplasticity
[25] Information theory – by Wikipedia: https://en.wikipedia.org/wiki/Information_theory
[26] Information Theory and Prairie Dogs – by Donald McIntyre: https://etherplan.com/2020/09/23/information-theory-and-prairie-dogs/12692/
[27] Handicap principle – The peacock tail in flight, the classic example of a handicapped signal of male quality – by Wikipedia: https://en.wikipedia.org/wiki/Handicap_principle
[28] Moose Rutting in Denali – by the National Park Service (NPS), U.S. Department of the Interior: https://www.nps.gov/articles/denali-moose-rut.htm
[29] Imperator – by Wikipedia: https://en.wikipedia.org/wiki/Imperator
[30] Barracks Emperor – by Ancient History Encyclopedia: https://www.ancient.eu/Barracks_Emperors/
[31] Shelling Out: The Origin of Money – by Nick Szabo: https://nakamotoinstitute.org/shelling-out/
[32] Artifacts of wealth: patterns in the evolution of collectibles and money – by Nick Szabo: http://unenumerated.blogspot.com/2016/07/artifacts-of-wealth-patterns-in_15.html
[33] Alpha (ethology) – by Wikipedia: https://en.wikipedia.org/wiki/Alpha_(ethology)
Code Is Law