You can listen to or watch this article here:
Yet another of the brilliant solutions, perhaps one of the most important ones, that Satoshi Nakamoto created when building Bitcoin was to solve the famous Byzantine Generals Problem in distributed systems. This means that, rather than 33% -1 fault tolerance, Proof of Work based blockchains have up to 50% fault tolerance.
However, what Satoshi really did was actually to avoid the problem, rather than solving it directly, by establishing an external physical signaling system: Mining.

As an external physical signal, it resembles the signals earth receives from outer space, which are uncontrollable, therefore unforgeable by humans.
For example, when laser interferometers on earth detect gravitational waves, those are truly “trustless” because it is impossible for humans to forge such signals, and whoever has a detector (scientists in the US, European Union, China, India, and others) can actually verify the signal directly from the source.
However, mining in proof of work based blockchains is not totally “trustless” as many confuse, it is really “trust-minimized” because if a sufficient number of miners collude to reorganize the blockchain, they can actually do it. This threshold is the famous “51% attack”.
Highly secure blockchains such as Bitcoin and Ethereum Classic (ETC) use the proof of work based consensus mechanism created by Satoshi Nakamoto, thus called Nakamoto Consensus.
Division of Power Between Miners and Full Node Operators
The good news is that, in proof of work based networks, full nodes actually have an additional very powerful recourse to defend themselves from potentially malicious miners: To split from them.
The above can be done by rejecting blocks by implementing a User Activated Soft Fork (UASF), or by outright “firing” or excluding miners from the network by changing the mining algorithm, which would render their mining equipment, and thus capital investment, useless.
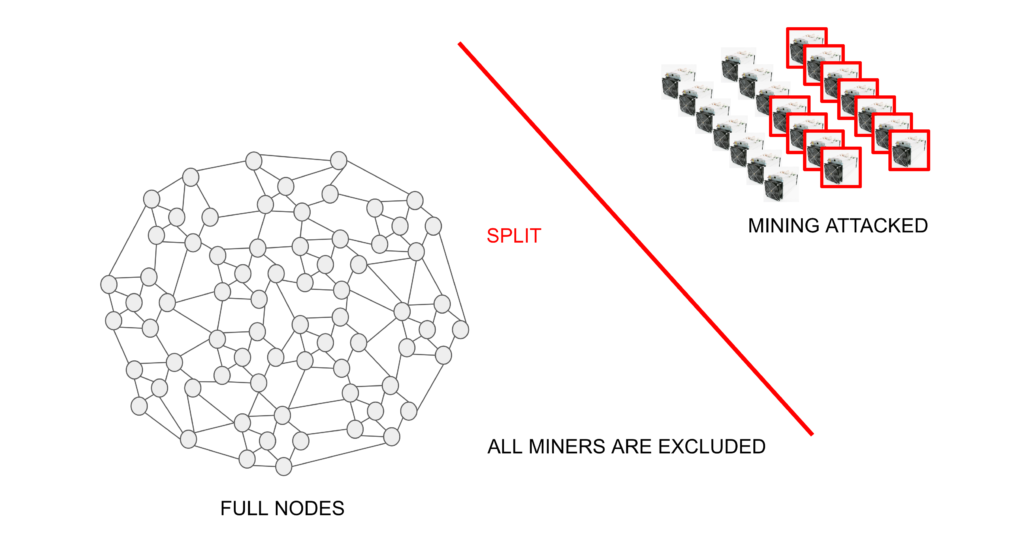
The ability to split from miners, when and if they behave maliciously, constitutes a very powerful symmetrical division of power in any proof of work based operating network such as Bitcoin or Ethereum Classic. This is because the standing threat of being excluded is an important deterrence for miners to build blocks with different rules, reorganize the blockchain, make double spends, or disturb network liveness and safety in any way.
Division of Power Does Not Exist Between Validators and Full Node Operators in Proof of Stake Distributed Ledgers
Note that I wrote “distributed ledgers” in the title above. This is because proof of stake networks are not blockchains. “Blocks” are only made by miners in proof of work based networks using enormous amounts of energy, similar to the large events in space that are detected on earth. All the other digital asset networks using the format and terminology of “blocks” just do that to make the market believe they are “blockchains” to appeal to the authority of Bitcoin and Ethereum Classic.
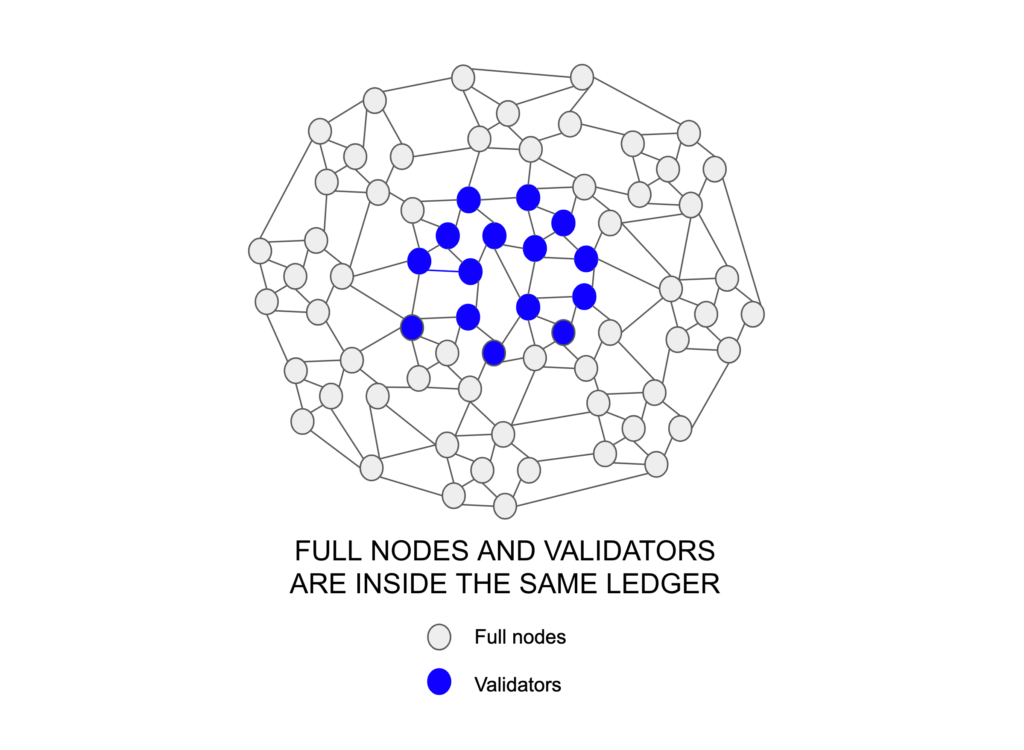
Moreover, proof of stake distributed ledgers do not have the division of power that proof of work based blockchains have. This is because the way those networks are organized is that, of all the nodes, only a subset, the validators (sometimes called Stakers, Block Producers, Bakers, Masternodes, etc.) are the ones who collect, produce, and enter new data batches into the distributed ledgers. As the form of becoming validators is by depositing a digital currency (stake) in their accounts, that means that they are inside the same ledger as the rest of the nodes.
What the above organizational structure creates is that if there are attacks by malicious validators, and the full nodes and the remaining honest validators want to split, they actually carry the attackers with them to the new distributed ledger.
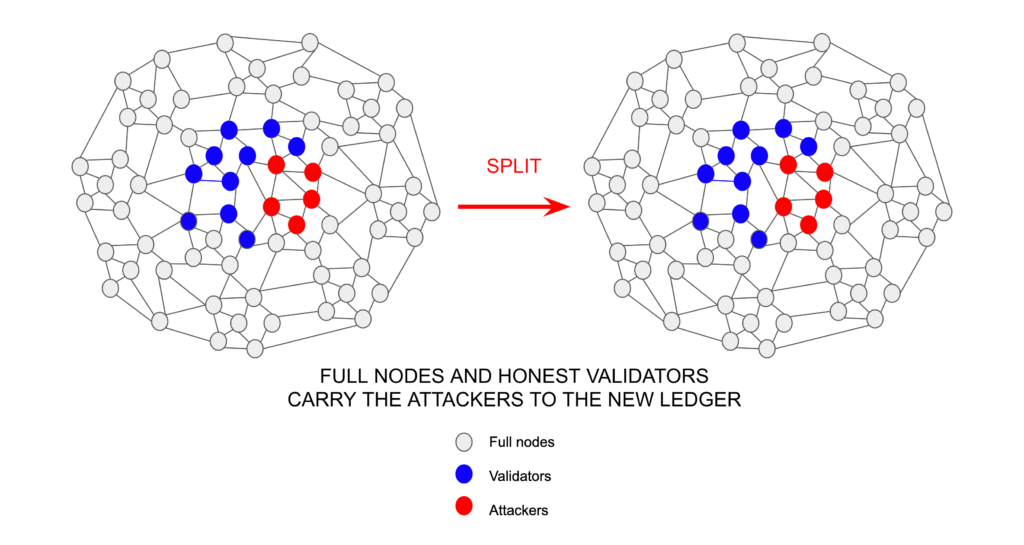
This is a huge weakness in proof of stake systems because it means that the only nodes with any power are the subset who are established as validators. They are under no threat of being “fired” or excluded from the network unless a cardinal rule in trust-minimized networks is broken: Immutability of accounts, smart contracts, and balances.
The above is because some theorists believe that “social consensus” or “weak subjectivity” in proof of stake means that a hard fork to exclude the malicious validators from the distributed ledger, for example by deleting their accounts and balances or confiscating their deposits, would be a perfectly fine action. This philosophy was, in fact, applied when TheDAO attacker was neutralized from the Ethereum network in 2016 by means of a hard fork that implemented an irregular state change.
However, the reality is that such arbitrary interventions as described above only confirm that the proof of stake design is fundamentally flawed for high security use cases.
The other important thing that this exercise shows is that the true fault tolerance in proof of stake networks is 33% -1 of the subset of nodes who are established as validators, this means, the subset of the subset. That is an extremely weak security threshold.
Conclusion
There are other serious security vulnerabilities in proof of stake distributed ledgers below their fault tolerance. These include, that validator entries in the ledger do not accumulate work, therefore reversing the whole chain to genesis is trivial, while in proof of work based blockchains, the accumulated work in the chain since the genesis block actually makes it practically impossible to reverse the blockchain, even if miners have 100% of mining power.
The other vulnerability is that the absence of an objective fork choice when there are network splits, such as the most accumulated proof of work, does not minimize Sybil attacks. In proof of work based blockchains, that objective fork choice minimizes Sybil attacks because, as long as a node is connected to at least one honest node, it is easy to always select the best version of the chain.
As to symmetrical division of power, it exists in proof of work based blockchains because the signal that miners send to the network of full nodes is produced and sent from totally external sources. This means that full nodes have the option of “firing” and replacing such external sources, if they become systematically or significantly corrupted, without violating immutability of the ledger, accounts, smart contracts, and balances.
Such division of power does not exist in proof of stake distributed ledgers making them significantly more vulnerable. That makes proof of stake networks perhaps more adequate for higher performance, but less secure tasks in the digital asset industry.
My thanks to Hugo Nguyen for helping me confirm the absence of “Division of Power” between proof of stake validators and full nodes: https://twitter.com/TokenHash/status/1113285028849442817