This article describes an idea that may introduce better node counting and identification features on a proof of work blockchain, albeit sacrificing some anonymity and introducing some private key risk to the network.
The goal of counting and identifying nodes is to be able to ostracize dishonest nodes from the network automatically or manually. What constitutes a “dishonest node” is easier to judge when it means objective deviations from the operating network protocol rules. For this, some automated retaliation and response strategies are introduced. For subjective bad behavior at the social layer, manual retaliation and response strategies may be implemented, however these would require much more coordination efforts at the social layer.
The base idea of ClanChain stems from evolutionary biology in the form of DNA kinship identification in social animals [1] such as humans. For this reason, I will use some anthropomorphism to explain the design and perhaps characterize how “evolutionary” payoffs and costs play out to coordinate the behavior of all types of network nodes.
The underlying ClanChain network is a single proof of work blockchain identical to Bitcoin [2]. The genesis block hash is not only the first hash on which future blocks are built on, just like Bitcoin, but is also the “original DNA genome” from which all the nodes in the network get their own unique DNA and are identified and classified by all the other nodes in the network at the protocol layer.
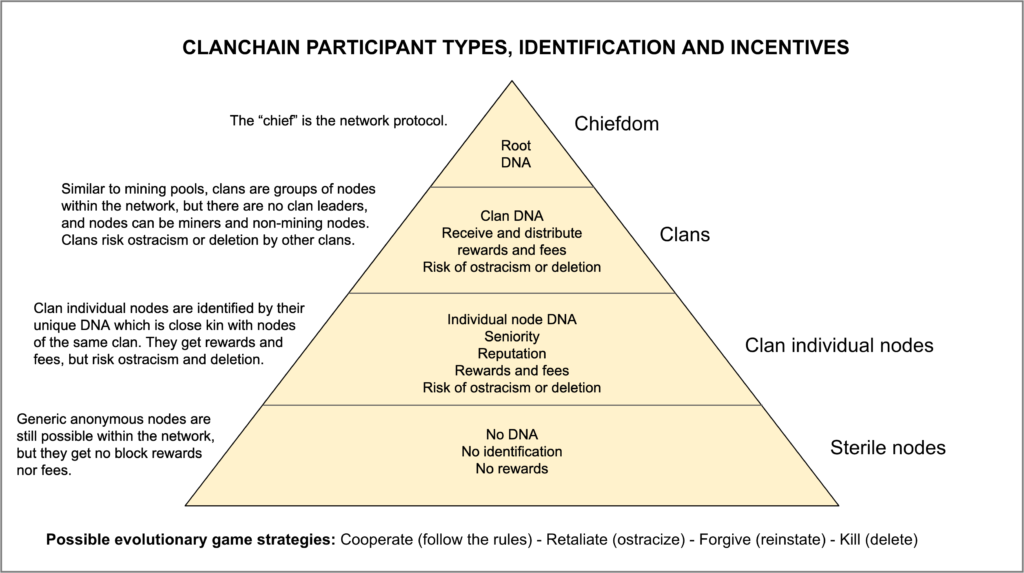
1. Participant Types
The metaphor is that the network is a clan system [3] organized as a single chiefdom. Each clan is composed of many individual nodes who all share closer kinship than with nodes of other clans.
Chiefdom
The chiefdom is the unified network which has the genesis block with a genesis hash which is the source of all the “gene pool” of the network.
Clans
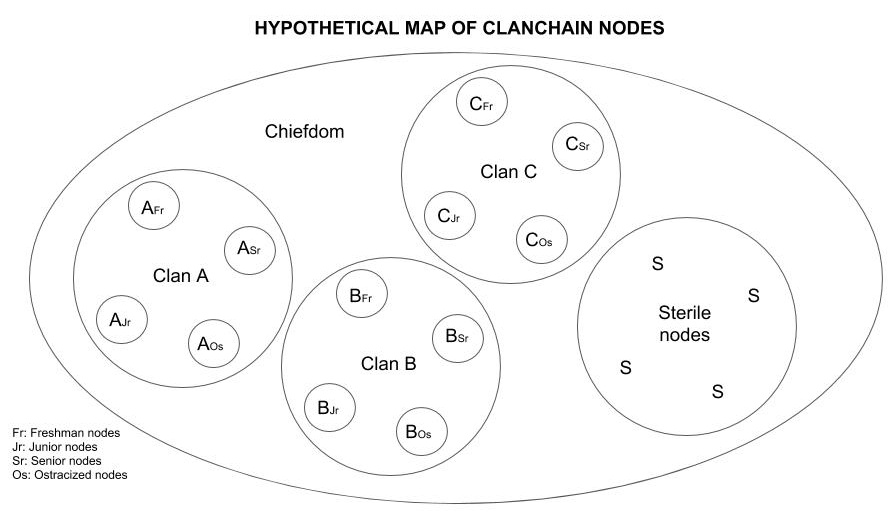
Clans are subsets of nodes within the whole chiefdom. They behave like mining pools, but in this case they are composed of both miner-nodes and full-nodes. Clans derive their DNA from the genesis hash, but one clan of nodes has a specific sub-hash that identifies and unifies it similar to normal family groups.
Clan Individual Nodes
Clan individual nodes are normal miners or non-miner full nodes. When they join the network permissionlessly they select to which clan they want to belong. When they join a clan their private key is associated with the DNA of the clan and a single DNA genome is created for the individual node. This individual DNA is not related to the node software, but to the private key. The individual node DNA is used to sign transactions, clan mining shares submissions, and new blocks found if any. If the node is not a miner, it can only validate transactions for which it also receives some rewards and fees (see Rewards and Punishments section below).
Ostracized Nodes
Ostracized nodes are clan individual nodes who behaved badly by either trying to send double spends, bad blocks, trying to split the network, spamming, or other malicious activities. These nodes are deprived from any rewards from the clan, but can stay in the network until a number of blocks, say 1000, has passed as punishment, then they can rejoin. If a node is consistently malicious it can be permanently deleted manually from the clan and thus network.
Ostracized Clans
Ostracized clans are clans who behaved badly by permitting malicious behavior of their nodes, or are threats to the network for their behavior or oversized network share. These clans are deprived from any rewards from the chiefdom, but can stay in the network until a number of blocks has passed as punishment, say 2500. If the clan is consistently malicious it can be permanently deleted from the network.
Seniority (Freshman, Junior and Senior Nodes)
Freshman nodes are new clan individual nodes who receive a clan payout for participating, but with a discount for one year to prove loyalty to the kinship and that it is well behaved according to protocol rules. Junior nodes are the ones who passed to the second year and will suffer less of a discount for that year. Senior nodes are the ones who made it to the third year and will suffer no discounts, but will expire (die) in eight years. Senior nodes are the only participants in a clan that can exercise the power to vote to ostracize clan individual nodes or other clans.
Sterile Nodes
Sterile nodes are nodes that do not want to be part of a clan to preserve anonymity, but their participation has no rewards other than the right to enter transactions, validate transactions, and run a full anonymous node for personal verification purposes. Sterile nodes can choose to join a clan if they want to. Once they join a clan, their private key is permanently associated with an individual node, clan, and chiefdom DNA. They start as freshman nodes even if they were in the network as sterile nodes for longer time prior to joining a clan.
2. Clan System Rules
All the rules above can be coded and automated on the protocol and software. However, decisions to ostracize can also be entered manually by client operators.
Clans can only ostracize other clans or individual nodes of their own clan, but cannot ostracize individual nodes of other clans.
3. Identity
As expressed above, the whole network has only one genesis block hash, but that hash is the root to generate the DNA of each clan and each clan DNA is the root to generate the DNA of each clan individual node.
All activity in the system by any clan individual node must be signed with its individual DNA. The idea is that all the other nodes in the network and their specific clans must be able to identify all the activity by its signature the same way people identify other people by phenotypical features such as face, body, voice, colors, smell, etc. but in this case it’s “unique cryptographic DNA”.
All individual nodes enter transactions as part of a clan, to receive the benefits, or as sterile nodes with no benefits other than the ones explained above.
The first year, second year, and final eight year segments, thresholds, and overall lifecycle for node seniority above can be measured in blocks. When a certain amount of blocks have passed (e.g. 52,560 blocks is ~1 year) the node becomes a junior from a freshman and so on. Some additional security rules can be introduced in case nodes disconnect and reconnect frequently in practice.
Note that individual humans are not identified in this system, only the private keys. Bad or good behavior are judged by their actions within the network primarily. However, there is a component of subjective “social action” because nodes can ostracize other nodes or other clans by coordinating and entering their votes manually through their clients.
4. Rewards and Punishments
Seniority and Merit
Rewards are distributed inside clans by age of the nodes (e.g. freshman, junior or senior) and, in the case of miners, by amount of work contributed similar to how mining pools pay by share.
Behavioral “Natural” Regulation
As nodes age in the system and behave according to protocol rules they acquire higher shares in revenues, good reputation, and the right to vote. If nodes disconnect or cheat they will not have those benefits and run the risk of being ostracized or deleted.
The chiefdom (network) pays the rewards and fees per block to the wining clan. Then the clan distributes the revenues in the following way:
To Freshman Nodes
20% divided by all participating freshman nodes. Of this 15% is paid to miner nodes and 5% to non-miner nodes.
To Junior Nodes
30% divided by all participating junior nodes. Of this 22.50% is paid to miner nodes and 7.5% to non-miner nodes.
To Senior Nodes
50% divided by all participating senior nodes. Of this 37.50% is paid to miner nodes and 12.50% to non-miner nodes.
To Ostracized Nodes
zero.
[All the parameters and proportions above are examples. Payment to miners is further weighted by miner submitted shares. The values above can be adjusted to better fit the system incentive mechanism based on more research or careful thought!]
As it can be seen above, nodes that follow the rules have no consequences and may participate in clans to receive increasing rewards. Clan individual nodes who behave badly receive zero revenues and waste time and energy. Sterile nodes by choice don’t get any rewards either so they are a minor threat, and if they enter bad transactions or spam they can just be rejected as in the Bitcoin network’s normal defense mechanisms.
4. Contentious Upgrades and Forks
When individual nodes, whether they are members of clans or not, prefer not to follow new rules on the network they can split and create a new clan ecosystem.
5. Other Considerations
- Although the network is divided into clans who behave like mining pools, but where they can ostracize bad nodes on chain, all clans and nodes work on the same blockchain.
- Each new block on the blockchain has a hash that represents the previous block hash and the clan hash who found the block.
- Clans do not have a central node that submits blocks to the network, the protocol automatically identifies groups of clan nodes as single clans, there is no pool operator nor pool fees.
- It’s not clear if this kind of network will probably need an “eternal” rewards system meaning that rewards per block may be permanent rather than a 150 year decreasing distribution system as in Bitcoin. However, fees are the same as in Bitcoin.
- Nodes die after 10 years (freshman 1yr + junior 1yr + senior 8yrs) just to imitate real biological systems which seem to ensure decentralization and generational rotation so the “elders” and the “old rich guys and gals” die and let the new blood take over.
- In any case, real humans may have a “portfolio of honest nodes” so they can diversify their aging nodes. This also ensures that they don’t incur in so much single private key risk.
- Healthy node selfish behavior may help the network in the aggregate: As more nodes participate in a clan, the clan gets more share and the network becomes more secure. However, less nodes in a clan mean more revenues per node. This possible balance may help keep clan shares in the network below “dangerous levels”.
- I am not a computer scientist, but I speculate that such a genesis hash DNA genome per chiefdom, clan, and clan individual node may be achieved designing a clever Merkle-tree-like structure.
- I think that nodes may have to be able, as long as they are good behaving nodes, especially miners, to move from clan to clan to rebalance hash power per clan or to escape censorship. This may mean that clans may have to accept migrating nodes with their reputations and seniorities. However, if they behave badly in their new “family”, clans may still have the option of ostracizing them.
6. Attack Vectors and Retaliation or Response Strategies
1. Sock puppet attack
This vector means that one person or group can create as many clan individual nodes as they want, multiplying in quantity to gain economic and voting power within one or more clans. The retaliation strategy by a single clan under attack is to identify the nodes which are performing the attack and ostracize or delete them. In this case this action could be performed manually. The other strategy is that all the honest nodes can migrate to other clans (carrying their reputations and seniorities) or start a new clan (not carrying their reputations or seniorities). If the legacy malicious clan turns into a threat to the entire chiefdom, then the other network clans may decide to ostracize or delete it. A possible natural defense that the system may have is that it would take two years for all the sock puppets to gain such economic and political clout in any given clan.
2. Censorship of Individual Nodes
Censorship of individual nodes for non-technical or political reasons can be responded by the victim node by migrating to another clan carrying its reputation and seniority. However, if the same node is censored by all other clans as it migrates or participates in those clans, then it may be a signal that it is generally a badly behaving node! In this case, the best response by the node operator is to start with a new node and behave “nicely” i.e. according to network rules.
[As I think of more attack vectors or as they are suggested to me, I will add them here.]
7. Conclusion
I think the benefits of the above scheme for a Bitcoin style proof of work network such as ClanChain are:
1. By participating in a clan, nodes have the advantage of scale, similar to a mining pool, and revenues whether they are miner or non-miner nodes.
2. If nodes behave according to rules they can gain the benefits of good reputation, seniority, and increasing internal share in the revenues of the clan.
3. Everybody in the network knows who cheated or who was ostracized i.e the long term memory of every clan individual node is preserved.
4. As the network is divided in clans, rules are largely integrated in the protocol, and nodes are identifiable, ostracizing clan individual nodes does not require hard forks, network wide coordination, nor very long social discussions.
As the design of ClanChain encourages cooperation first, retaliation second, possible forgiveness third, and tangible drastic deletion last [4], it may result in less aggressive behavior amongst network participants (e.g. less contentious hard forks and splits) and significantly reduce “violence” while increasing time and energy spent in productive negotiations and social agreement.
References
[1] The Logic of Animal Conflict by J. Maynard Smith and G. R. Price: http://etherplan.com/the-logic-of-animal-conflict.pdf
[2] Bitcoin: A Peer-to-Peer Electronic Cash System: https://bitcoin.org/bitcoin.pdf
[3] Clans: https://en.wikipedia.org/wiki/Clan
[4] Evolutionarily Stable Strategies: https://en.wikipedia.org/wiki/Evolutionarily_stable_strategy