You can listen to or watch this video here:
The purpose of the Bitcoin (BTC) network is to avoid trusted third parties by hosting and maintaining a decentralized ledger with sound money in a peer-to-peer, fully replicated, global blockchain.
The question is, what components guarantee the integrity and safety of the network?
The Combined Security Model
To answer the question, the system may be divided in two parts: The deployed operating network, which works in a mechanical way according to a set of objective rules, and the social layer, which is the sum of people who develop and run the operating network on a global scale.
The model is combined because it addresses the security of the operating network by using proof of work as a physical component, and the security of the social layer by using the coordination problem as a political component.
In other words, proof of work makes it very costly to attack the system computationally, and the coordination problem makes it very costly to attack the system socially.
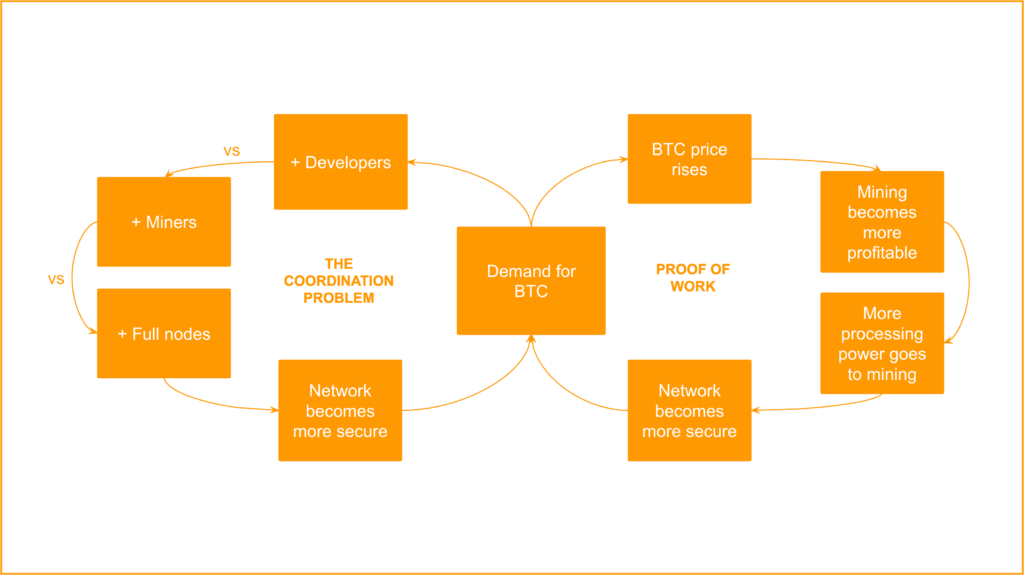
However, as seen in the diagram above, the proof of work and coordination problem mechanisms are not only about imposing costs, but also about economic incentives. This article explains both sides of the model.
Proof of Work
The physical proof of work security mechanism is a virtuous circle that has several components which reinforce each other:
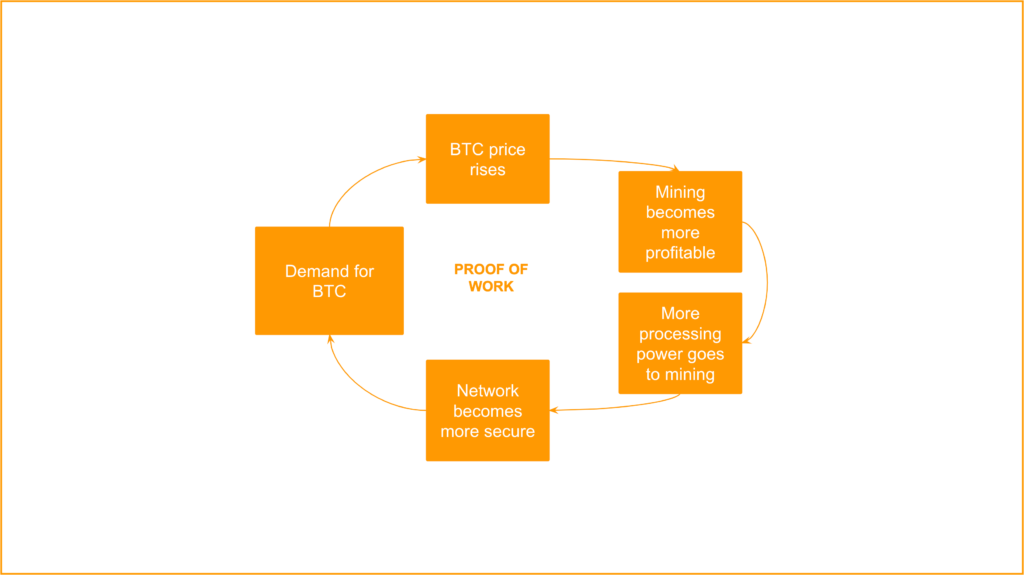
1. Demand for BTC:
The terms “decentralized ledger” and “sound money” are proxies for security. This means that as Bitcoin becomes more secure, its service, a decentralized ledger for sound money, becomes more valuable. As the demand for its service increases, then the demand for its native token, $BTC, also increases.
2. BTC Price Rises
When demand for $BTC increases, then its price rises in the market. The rising price of the native token is complemented and prompted by BTC’s sound monetary policy.
3. Mining Becomes More Profitable
In proof of work networks, miners compete to win the rewards of the blocks they find in the network. To increase their chances of earning the rewards, they invest in mining gear so they can increase their hash rate. This investment has a higher payoff as the price of the native token rises, therefore increasing miner profitability.
4. More Processing Power Goes to Mining
As miners invest in more and better gear, more processing power goes to mining, therefore, collectively, they increase the aggregate hash rate of the network.
5. The Network Becomes More Secure
As the aggregate hash rate of the network rises, it constitutes a security barrier for hackers to physically attack the network. As the network is more costly to attack it becomes more attractive, therefore increasing demand for BTC, thus reinforcing the system.
The Coordination Problem
The political coordination problem security mechanism is a complementary and adjacent virtuous circle that also has several components that reinforce each other:
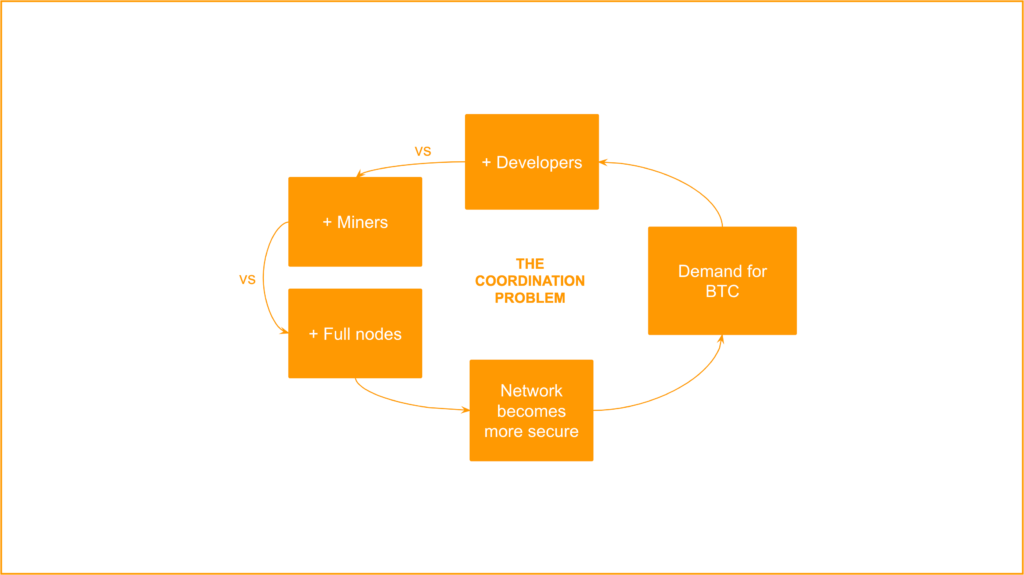
1. Demand for BTC
As the proof of work virtuous circle makes the network more secure, Bitcoin becomes more valuable, therefore increasing demand.
2. More Developers
A rise in demand for BTC incentivizes more core developers, who may be from different regions and cultures, to participate in the network either contributing to the existing core client, or building new node clients. Non-core developers who build applications or layer 2 systems that work on top of Bitcoin may also be incentivized as the network becomes more secure for their users.
3. More Miners
As higher demand for BTC incentivizes more developers, and induces to higher $BTC prices, it also attracts more miners, not only in the form of hash power, but also in the number of miners, who may also be from different regions and cultures.
4. More Full Nodes
More developers, miners, and a higher value of the network in general, attracts more full node operators, such as exchanges, wallet providers, infrastructure services, layer 2 systems, block explorers, and application startups. All these services make the network more attractive and valuable for investors and users in general, who may also increase in numbers.
5. The Network Becomes More Secure
As a combination of developers, miners, full node operators, investors, and users increase their participation in the network from multiple regions and cultures, it becomes extremely difficult for subsets of those participants to collude to attack the network, either at the social political layer or even at the physical layer. As with the proof of work component, this level of security makes the Bitcoin blockchain more attractive, therefore increasing demand for BTC, thus further reinforcing the system.
If the System Is So Secure and Immutable, How Are Bugs Fixed or Upgrades Made?
As all constituents and participants mentioned above dedicate more time and money developing, operating, investing in, or using the network, their general incentive is for the network to keep its integrity as much as possible. As mentioned above, this makes it very difficult to coordinate attacks, but the same incentives mean that, collectively, they have an interest in the network functioning correctly as intended and designed.
When unforeseeable bugs, flaws, or even catastrophes occur in the network, these positive incentives builtin in the system actually make it easier and more probable for all participants to coordinate to fix them, or even to make upgrades to the system with much needed or desirable features.
Examples of such occasions in Bitcoin have been the urgent fix of the 2010 overflow bug, the 2013 chain split, and the SegWit upgrade, which actually followed a war over the network’s block size.
In Ethereum Classic, which has a very similar security model as Bitcoin, examples have been the deactivation of the difficulty bomb, the change of its monetary policy, and the Atlantis, Agartha, and the upcoming Phoenix upgrades.
Conclusion
Another complementary component that helps with coordination at the political social layer, when changes or fixes are not controversial, is the Bitcoin Improvement Proposal (BIP) process, which is a rigorous standards setting system for developers, engineers, scientists, and other participants to propose them to the BTC ecosystem. When, and if, the proposals pass through several stages, then they may be implemented in the operating network, which means that it still needs the consensus of node operators and miners to happen.
In the physical proof of work side, another feature that significantly contributes to the security of the mechanism is the fact that there is division of power between miners and full nodes, so full nodes can literally fire miners in the unlikely scenario they systematically attack the blockchain, which is a strong deterrent in itself.
All in all, the overall effects and benefits of the trust minimization enabled by the combined security model, and complementary processes and features described in this article, are social scalability, global seamlessness, and permissionless access of Bitcoin worldwide.
The proof of work security model in this article was inspired by the book “The Bitcoin Standard: The Decentralized Alternative to Central Banking” by Saifedean Ammous.
The complementary and adjacent coordination problem security model is based on Etherplan’s research.
Code Is Law